 An article in Ars Technica reveals that the NSA can do a lot more than just store people’s metadata for a while. The NSA actually has the capability to passively scan the Internet for computers with vulnerabilities that it knows how to exploit. It can also look for computers that may have already been in exploited in ways that the NSA can use to its own advantages. It goes still further than this.
An article in Ars Technica reveals that the NSA can do a lot more than just store people’s metadata for a while. The NSA actually has the capability to passively scan the Internet for computers with vulnerabilities that it knows how to exploit. It can also look for computers that may have already been in exploited in ways that the NSA can use to its own advantages. It goes still further than this.
Document Authors
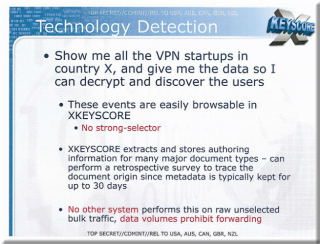
The XKEYSCORE system that was revealed via the leaks provided by Edward Snowden was already known to be far more powerful than was ever stated publically before the leaks. It’s powers, however, extend to being able to track VPN usage from some nations and to being able to get metadata that the NSA could later use to break PGP encryption. According to the article, the NSA usually keeps this data for 30 days, making it possible for them to go through that data later, if they choose. According to the documents leaked by Snowden, a user could look at all the VPN connections started up from a given nation and use that data to determine the user of that connection.
The system can also go through many major document types and look for author information. This, of course, can be used on the data that the NSA stores, making it possible for them to scan for author information after they’ve had the data collected for some time.
The top secret documents boast that no other system can do this on bulk traffic. That, of course, means that the data is simply gathered and scanned through at random and that it is not a targeted search of data known to belong to someone who is under surveillance.
What it Means
The NSA can scan an entire nation for machines that it can exploit. It can scan an entire nation for VPN connections starting up and go through that data to find out who is using those connections. It can also scan emails and other documents for information that it can use to decrypt any PGP encryption with which they have been provided.
This information goes far beyond the metadata that the NSA first claimed that was its only target. With the NSA having recently opened up a huge new datacenter, there’s no doubt that they are sorting through this type of data now, without warrants, transparency or accountability.


Hi,
I’m seriously confused about VPNs, TOR and the NSA. Some sites say that the NSA can’t crack VPNs, other sites say YES, they can. TOR gets you added to the “Persons of Interest” list and so on.
Does anyone know the truth?
Let’s assume that I’m a “Person of Interest”, for the sake of argument OK? Maybe I use TOR, maybe I blogged 911 was an inside job, etc. So now the NSA monitors every bit of data going through my ISP, which is a cable modem FWIW. The router is an Asus AC-3200 which connects with OpenVPN to my VPN, which is ExpressVPN. It uses RSA 2048 bit encryption and SHA 256 (AES) key sizes. BUT the NSA would have been there while I created my account and would have recorded any keys, passwords, etc. Then I connect to the router with a laptop which is booted from a TAILS usb, which has TOR pre-installed as part of TAILS.
Dnsleaktests show no leaks at all.
So, can the NSA listen in to everything I’m doing or not? Please, let’s set the record straight.
Thanks, Rob