Perfect Privacy may not be the least expensive VPN provider out there, but they are professional. A large network of servers, plenty of IP addresses and great encryption make this a service you may want to take a second look at.
Perfect Privacy is committed to the privacy and anonymity of its customers since 2008 and is one of the most secure VPN providers worldwide since the beginning. The protection of your privacy is our primary concern – therefore we do not record user activity.
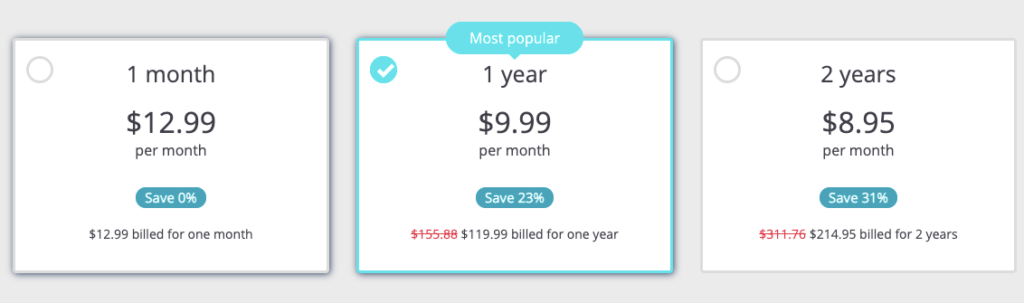
Pricing & Plans
Perfect Privacy plans all have unlimited bandwidth and options for different protocols, so the only differences are in terms of how much of a quantity discount you get.
Perfect Privacy is very flexible in terms of payment methods. You may use:
- PayPal
- Visa
- MasterCard
- UnionPay
- FasterPay
- GiroPay
- Sofort
- Mobiano
- Mint
- Bitcoin
- BitcoinCash
Free Trial/ Money-back Guarantee
Perfect Privacy doesn’t offer any free trials but has a 7-day money back guarantee.
Privacy & Anonymity
Perfect Privacy does not store any of your data. They have created their server infrastructure so that it is not possible to record data at all. The data, therefore, runs on ram disks to ensure that there is nothing left when a server is disconnected from power. If you are worried that a security agency could intercept a server while it is running, use a cascaded connection as mentioned above.
Provider Logging Policy
Perfect Privacy’s technical infrastructure has been designed and built with the requirement to collect only the absolute minimum of data necessary to operate the servers.
Specifically, they do not record or log any user traffic so potential sharing such data with third parties is technically impossible. They do not store IP addresses, access times or duration, nor bandwidth caused by individual users
For the operation of the servers, displaying general server information on the website and for the detection and elimination of potential technical problems, they record the total load of the individual servers. No conclusions about a user’s identity can be drawn from this data.
Torrent Policy
You can encrypt torrent data using this service. There are no restrictions on protocols given.
Customer Support
Perfect Privacy has a Help Center available on their website which includes manuals, an FAQ page and forums. They also have a ticketing system where you can submit questions or seek technical support.
Product Testing
Perfect Privacy has apps for Windows, MacOS and Android. With the VPN App for Windows and the VPN App for macOS, you can also benefit from our unique Multi-Hop feature and cascade your Internet connection over up to four hops. That also means that the connection is encrypted four times.
With the VPN App for Android, you can effortlessly gain back control over your privacy without having to deal with complicated settings.
Perfect Privacy supports OpenVPN and IPSec. SSH 2 tunneling is also supported on this service.
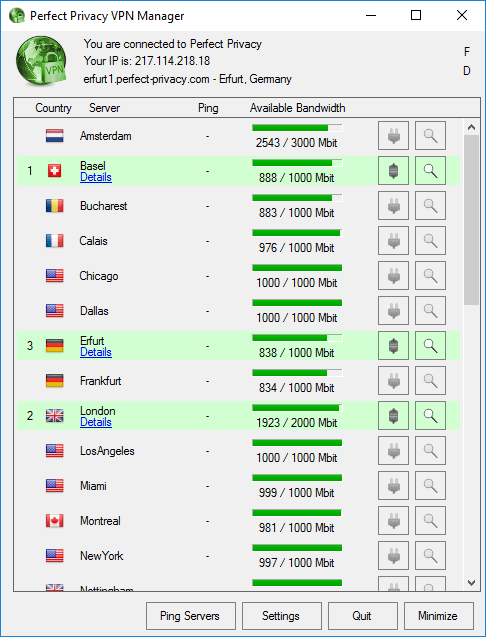
VPN Server Locations
Perfect Privacy provides you VPN-servers in 25 countries worldwide. At Perfect Privacy, they only use dedicated servers and entirely renounce virtual servers.
Countries Supported:

























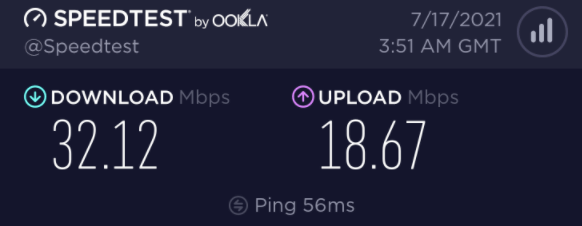
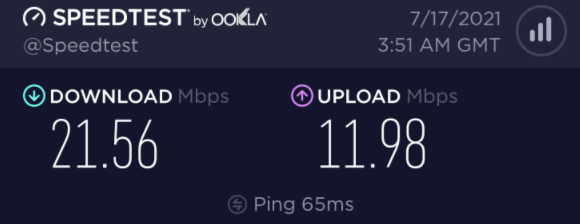
Speed Test
The high bandwidth surplus of the Perfect Privacy network guarantees you a working and fast VPN access at any time. They monitor the servers bandwidth utilization so that they avoid network bottlenecks, and provide new VPN servers if necessary.
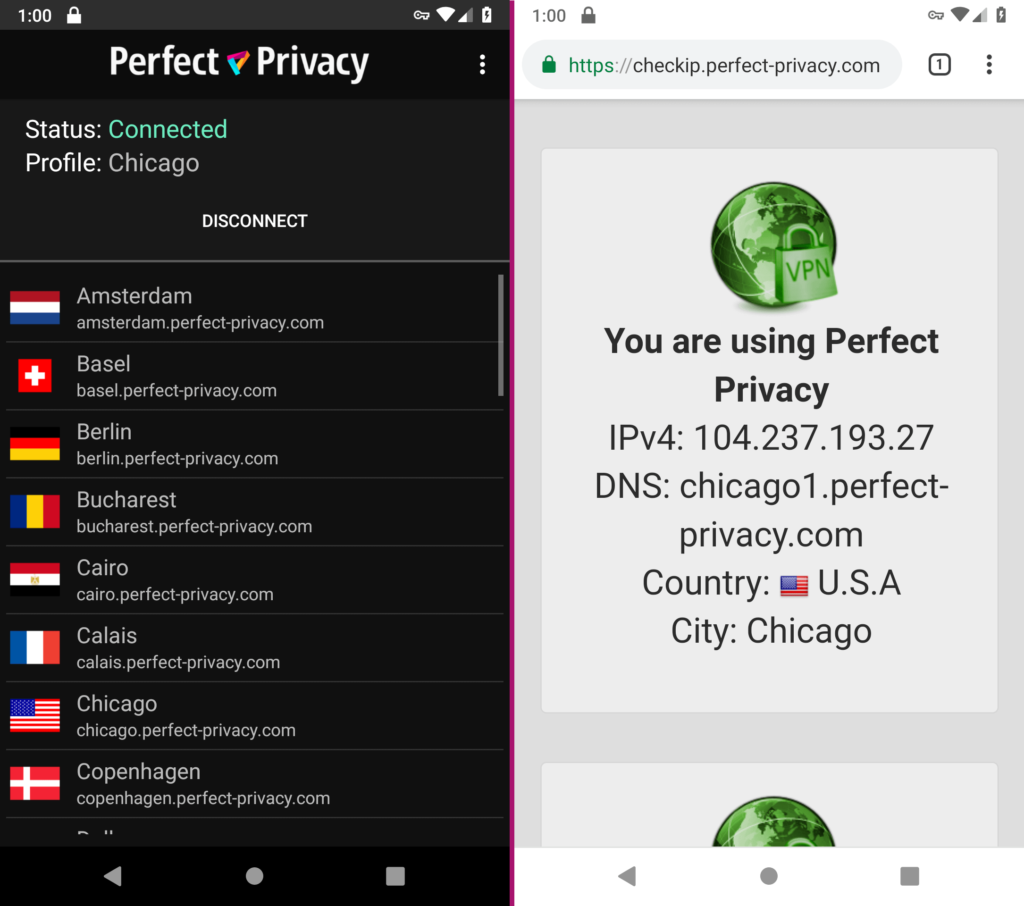
IPCheck and DNSLeak Test
Perfect Privacy successfully masked our IP address and did not leak our DNS server.
Feature Summary
- No logging/ log-files
- For all your devices
- Up to 1000Mbps bandwidth
- Cascading of multiple VPN servers
- IPv6 Support
- Multi-hop VPN
- Kill Switch
- VPN Protocols – OpenVPN, IPSec, SSH2
Additional Bonus Features
- NeuroRouting – ensures that your data remains within the strongly encrypted VPN network of Perfect Privacy for as long as possible. A neural network and our algorithms constantly calculate the best routes for your destinations on the Internet.
- TrackStop – a filter that blocks content from untrusted or unwanted sources. Stop annoying advertisements. Defend yourself against social media tracking. Block harmful phishing and malware websites. Protect your children from inappropriate content. Individually adjust the filter settings according to your needs.
- Stealth VPN – a method to counter Deep Packet Inspection (DPI). In some restrictive networks and countries, it is used to detect and block VPN traffic. Stealth VPN masks the VPN packets and makes them look like regular HTTPS packets.
We Liked
Perfect Privacy has a good and clear logging policy.
Areas for Improvement
Perfect Privacy is not an inexpensive service. There are companies out there that offer similar services for less money. This is not a lacking service at all, however.
Conclusion
Perfect Privacy is a very well-designed service with good security. They don’t log user activity or restrict protocols, which makes them a good choice for those who want privacy. There are also plenty of options as to how you connect to their servers.
There are a lot of IP addresses available, though they cannot be assigned permanently or randomized. There are other services that offer those options. Overall, however, Perfect Privacy does a good job of offering what it promises.


Leave a Reply